Endpoint Protection
Safeguard Your Business with Modern Endpoint Protection
Why Endpoint Protection Matters
Endpoint protection is evolving to meet the demands of hybrid workforces, advanced cyber threats, and compliance requirements. Today’s solutions combine hardware-based security, AI-driven threat detection, and seamless management—empowering organizations to defend every device, user, and workload. Explore how leading OEMs, silicon providers, and software innovators deliver layered protection, and discover the right endpoint security for your business.A Guide to Calculating Endpoint Protection ROI
How to Quantify the Business Value of Modern Security Investments
Security leaders are often asked a deceptively simple question: “Is our endpoint protection worth it?” A practical way to answer is to quantify what you save, what you avoid, and the time you get back.Endpoint protection ROI compares the value your endpoint program delivers, including cost savings, reduced breach risk, and team efficiency, against what it costs to purchase, implement, and run it over time. This article walks you through a straightforward endpoint protection ROI framework you can adapt and use with data you likely already have.

What Is Endpoint Protection ROI?
Before we get to the calculations, let’s align on terms. Endpoint protection means tools and practices that protect laptops, desktops, and mobile devices against modern threats. Today, this usually means a cloud-managed platform with antivirus, detection and response, patching, and automated remediation capabilities.Once you’re clear on what endpoint protection covers, the next step is to define the scope of your ROI model—the tools, people, time horizon, and which outcomes you’ll count—then calculate the ROI, or Return on Investment, by using a simple formula:
ROI % = ((Total Benefits − Total Costs) ÷ Total Costs) × 100
Use a common time horizon, such as 12, 24, or 36 months, and note the source of every assumption so the math is easy to verify or refresh later.
Start with these metrics:
- Unit costs you can monetize: Think cost per help desk ticket, cost per reimage, and a fully loaded hourly rate for SecOps or IT.
- Baselines: Use average monthly security tickets, malware-related reimages, and current mean time to repair (MTTR).
- A simple risk snapshot: Define an SLE (single loss expectancy) and an ARO (annualized rate of occurrence) that you and your risk team can defend.
Keep these inputs conservative and defensible to avoid overstating benefits and build credibility with stakeholders.
The Three-Pillar ROI Framework
Investments that matter are those that show clear financial outcomes. Converting endpoint outcomes into numbers lets you compare your endpoint protection investment with other initiatives on the roadmap. Think avoided operational spend, reduced expected loss, and hours you can redeploy to higher‑value work.Frame your endpoint ROI in three pillars that support an accurate calculation: cost savings (consolidation + fewer tickets and reimages), risk reduction (lower expected loss or ALE), and operational efficiency (hours you can deploy). Use the guidelines below to plug in your numbers and see the impact.
Pillar 1: Cost Savings
Modern endpoint platforms often replace overlapping tools and reduce on‑premises upkeep. Before you tally numbers, note where savings actually come from so you don’t double count later.
Where you may see savings:
- License consolidation: Retire overlapping tools and right‑size support contracts.
- Infrastructure and admin reduction: Move from on‑premises consoles to a cloud‑managed model and reduce server, upgrade, and hands‑on work.
- Incident handling avoided: Fewer malware reimages and fewer security tickets after prevention and rollback improvements.
How to calculate your savings:
- Tool consolidation (Year 1) = legacy spend avoided − one‑time migration/training
- Reimage savings (Annual) = reimages avoided × cost per reimage
- Ticket deflection (Annual) = tickets avoided × fully loaded cost per ticket
Pillar 2: Risk Reduction
Translate risk into dollars by estimating the expected annual loss you can avoid from endpoint incidents. Use the annualized loss expectancy approach to size it: ALE = SLE × ARO.
Key inputs at a glance
- SLE: Realistic “all‑in” cost of a significant endpoint‑driven incident (IR/forensics, legal/compliance, downtime, data loss, reputational work, sector penalties).
- ARO: How often such an incident is expected in a year.
How to calculate your risk reduction:
- Example:Before SLE $300,000 and ARO 0.4 → ALE_before $120,000. After ARO 0.2 → ALE_after $60,000. Benefit = $60,000/year.
Pillar 3: Operational Efficiency
Treat time saved as redeployable hours that let teams focus on higher‑value work without adding headcount.
Where the time comes from:
- Automation: policy‑driven patching, alert triage, quarantine or isolation, one‑click rollback.
- Faster MTTR: fewer L2/L3 escalations and fewer site visits with remote remediation.
How to calculate your efficiency gains:
- Time savings (Annual) = hours saved per week × 52 × fully loaded hourly rate
- Ticket reduction (Annual) = tickets avoided × fully loaded cost per ticket
Where to Pull the Numbers
You probably already have the inputs you need inside your existing systems. Here are the most practical places to pull them.Common sources:
- ITSM for tickets, reimage counts, and resolution times
- EDR or XDR console for detections, isolations, and rollback metrics
- Finance for unit costs, fully loaded rates, and tool spend
- Risk, Compliance, or Insurance for inputs to SLE and ARO and for recent incident detail
Compare the “How Much” to the “How Soon”
Looking at ROI and payback side by side helps you weigh return size against speed to value.At this point, you’ve tallied annual benefits plus annual and one-time costs. Convert these figures into a single, quarterly-refreshable view that shows both ROI percentage and payback months, and remember to use conservative assumptions and call out any exclusions.
First, calculate the roll-up:
- Total Benefits (Annual) = cost savings + risk reduction + efficiency gains
- Total Costs (Annual) = subscription or licensing + support + admin time
- One-time Costs (Year 0) = migration + training + services
Now compute:
- ROI % = ((Total Benefits − Total Costs) ÷ Total Costs) × 100
- Payback period = months until cumulative benefits pass cumulative costs
- 12-, 24-, and 36-month views for internal planning
Example: If Total Benefits = $800k and Total Costs = $400k, ROI = 100%, and if one-time Year 0 costs add $150k, payback occurs when cumulative benefits exceed $550k.
KPIs to Track Quarterly
Measure what you modeled so you can show impact, tune assumptions, and keep decisions anchored in data. A one‑page quarterly view makes trends (and gaps) obvious without chasing reports.Core KPIs:
- MTTR and dwell time, with a target of sustained reduction
- Infection rate and percent of endpoints in compliance with policy
- Reimages per month and security ticket volumePatch SLA attainment, such as critical patches within a set number of days
- Tool count after consolidation and ALE trend over time
Cadence that works:
- Review ROI and KPIs with finance every quarter
- Refresh assumptions annually or after major changes, such as fleet growth
Where ROI Models Go Wrong and How to Fix Them
Even a solid model can go sideways without guardrails, so make sure you set expectations up front.- Double counting: If a saving shows up under “cost,” for example, admin hours, do not also count it under “efficiency.”
- Ignoring one-time costs: Call out migration, training, and services separately in Year 0.
- Optimistic risk assumptions: If ARO is estimated, label it and provide the basis, such as history, insurance input, or a conservative benchmark.
- No stakeholder alignment: Share your assumptions with finance and risk before finalizing the model.
Tip: Prevent scope creep later by making sure you document any exclusions.
Deliver a Clear, Defensible Decision
Endpoint Protection ROI doesn’t have to be complicated. Start with a clear definition, gather a handful of baseline metrics, and quantify three things: what you stop paying for, what you avoid losing, and what time you get back. Roll those benefits against costs, show payback and multi-year views, and track KPIs quarterly.With a simple, transparent model, you offer a clear, defensible answer to “Is it worth it?”
Helpful next steps:
- Security Assessment Suite: Set defensible loss (SLE) and asset risk operation (ARO) figures using real evidence so your risk math isn’t guesswork.
- Modern Device Management: Cut reimages and ticket volume with automated patching and configuration.
- Managed & Monitored Security Services: Get 24×7 detection and response that lowers the chance and duration of endpoint incidents and helps prevent small issues from becoming costly outages.
Device-driven Defense: How Leading Brands Secure Your Business
Dell
Dell Trusted Devices
Comprehensive Endpoint Security
Dell delivers the world’s most secure commercial PCs with layered endpoint protection that combines hardware-based security, advanced threat detection, and intelligent telemetry. Solutions like SafeID, SafeBIOS, and Trusted Device help businesses stay ahead of evolving threats.
The Anatomy of a Trusted Workspace
Improve the Security of Your Fleet with Multiple Layers of Defense
Discover how Dell Trusted Workspace delivers multilayered endpoint security—combining exclusive hardware, firmware, and supply chain protections with advanced software and telemetry—to help businesses stay resilient against modern cyber threats.The Hidden Layer of Protection: How BIOS Security Can Safeguard Your Business
Dell SafeBIOS delivers exclusive below-the-OS protection with off-host BIOS verification, Indicators of Attack, and automated tamper alerts. Integrated with Dell Trusted Device telemetry, it empowers IT to detect, analyze, and remediate threats before they impact business.HP
Why HP for Endpoint Security?
HP Workforce Security Solutions deliver end-to-end protection for hybrid workforces, combining hardware-enforced isolation, Zero Trust architecture, and advanced threat intelligence. Unique features include micro-virtualization to secure privileged tasks, remote tracking and erasing of lost devices, and seamless integration with existing security tools. Centralized management and tailored policies ensure compliance, productivity, and robust defense against ransomware, phishing, and emerging cyber threats—setting HP apart for organizations seeking reliable, scalable endpoint security.
Endpoint Isolation
A Superior Approach to Endpoint Protection and SOC Efficiency
Explore HP’s Endpoint Isolation: hardware-enforced micro-VMs, introspection, and cloud analytics deliver Zero Trust protection, superior threat containment, and seamless user experience—setting HP apart in endpoint security.
HP Sure Click Enterprise
HP Sure Access Enterprise uses hardware-enforced isolation to block malware, secure privileged access, and integrate with existing tools—delivering data sovereignty, seamless compliance, and a superior user experience. Isolate threats, protect credentials, and deliver real-time threat intelligence—offering seamless, policy-driven security that sets a new standard for endpoint protection.
HP Wolf Pro Security
Comprehensive PC Security, Made Simple.
HP Wolf Pro Security delivers hardware-enforced isolation, AI-driven threat protection, and credential safeguards—offering simple, cloud-managed endpoint security proven to stop phishing and ransomware for small and mid-sized organizations.
HP Sure Access Enterprise
HP Sure Access Enterprise uses hardware-enforced isolation to secure privileged access, block endpoint malware, and integrate with leading security tools—delivering seamless compliance, data sovereignty, and a worry-free user experience.HP Wolf Protect and Trace
Remotely Track and Secure PCs
HP Wolf Protect and Trace enables real-time tracking, locking, and erasing of PCs—even offline with Wolf Connect—delivering advanced asset management, data security, and compliance for modern device fleets.
Lenovo

Lenovo ThinkShield Solutions
Comprehensive Protection for Small and Midsized Businesses
Discover Lenovo ThinkShield: unified, AI-powered endpoint protection for small- and medium-sized businesses. Benefit from seamless integration, layered defense, and tailored plans—delivering advanced security, simplified management, and end-to-end compliance.Apple
Securing the Apple Ecosystem
Privacy by Design, and Enterprise-ready Protections for Every Device
Discover how Apple’s unique integration of custom silicon, hardware, software, and services delivers industry-leading, end-to-end protection, privacy, and seamless management for every device and business need.
Samsung

Samsung Knox Suite
Built for Business. Optimized for Samsung Galaxy.
Samsung Knox Suite is an all-in-one solution for securing and managing Samsung Galaxy devices. It offers advanced device management, analytics, remote support, and unique features like hardware key remapping and barcode scanning—streamlining IT workflows and empowering business mobility.Core Strength: How Processors Power Endpoint Security
AMD
AMD Enables Secure Business PCs
Securing Business PCs From BIOS to Browser
Discover how AMD’s business-class PCs deliver advanced endpoint protection from BIOS to browser. Unique hardware-based security features help safeguard data and system integrity, meeting the demands of today’s complex threat landscape and supporting modern security frameworks. Learn how these solutions set a new standard for secure, high-performing devices built for future workloads, including AI.
Inside Access: HP EliteBook X G1A Security and Manageability
Ensure work gets done securely, smoothly, and on time with HP EliteBook X G1A with AMD Ryzen™ PRO processors.Intel
Intel vPRO® Security
Intel vPro® delivers unmatched endpoint protection through hardware-based security that defends below the OS, safeguards applications and data, and uses AI-enhanced threat detection. Unique features like Intel® Hardware Shield, Control-Flow Enforcement Technology, and Total Memory Encryption set it apart—ensuring resilient, high-performance security for modern hybrid workforces.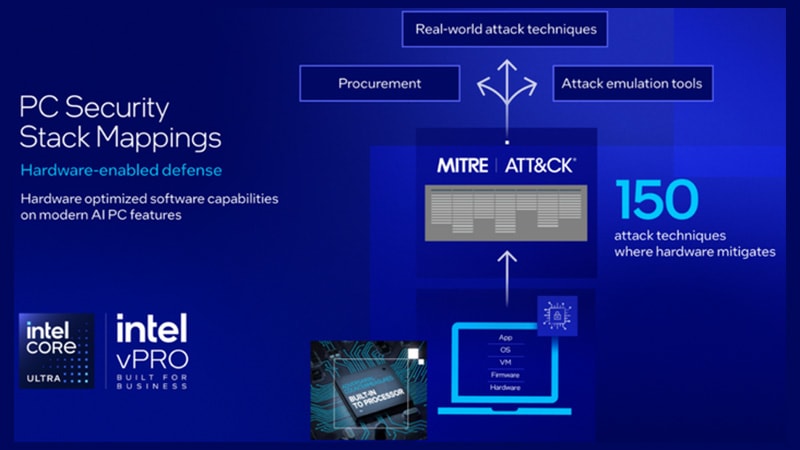
Intel vPRO® in AI PCs
Deliver an Industry Validated Defense vs. Real-world Attacks
Intel AI PCs with vPro® deliver industry-validated, hardware-enabled defense mapped to 150 real-world threat tactics via MITRE ATT&CK. Unique features like Intel® Threat Detection Technology, virtualization-based security, and iGPU-accelerated memory scanning empower security software to detect ransomware and fileless attacks with unmatched precision and performance.
Security Starts with Intel
Security Built In. Security to Build On.
Intel is a world leader in technology with a unique influence on cybersecurity. Discover the security practices that Intel uses and the products that Intel delivers to help safeguard customers.Intel views security as a responsibility to fulfill and a business opportunity for customers. In keeping with that responsibility, Intel works with many of the largest and most respected companies around the world, often in the most privacy-sensitive environments.

Windows 11 Security Starts with an Intel Hardware Foundation
A Secure Foundation Rooted Deep in Silicon
Discover how Windows 11 and Intel deliver next-gen endpoint security. From hardware-based isolation and firmware protection to AI-driven threat detection and zero-trust controls, this integrated approach safeguards devices, data, and users—empowering businesses to stay secure and productive.Qualcomm
Snapdragon® X Series Security
Securing The Modern Workforce
Snapdragon® X Series delivers chip-to-cloud security for modern workforces, featuring Microsoft Secured-Core certification, hardware-based encryption, Zero Trust frameworks, auto-healing resilience, and always-on 5G connectivity. Unique capabilities include trusted location geofencing, biometric identity, and real-time telemetry for proactive threat defense.
Featured Endpoint Security Solutions
Microsoft
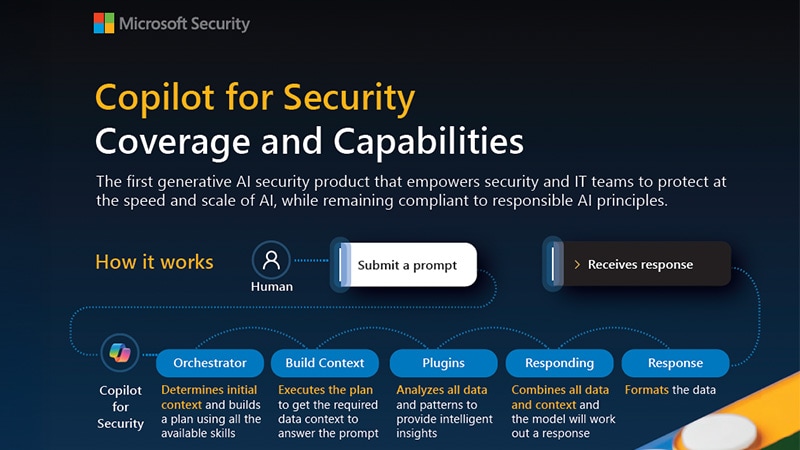
Copilot for Security
Experiences to Meet You Where and How You Work
Discover how Microsoft Copilot for Security leverages AI, integrated threat intelligence, and seamless cross-platform orchestration to deliver rapid, tailored endpoint protection—empowering teams with unique, advanced security solutions.How to Level-up Your Device Security with Windows 11 Pro Devices
On-demand Webcast
In this discussion, a panel of experts from Microsoft, Lenovo, and Connection share new insights into the need for hardware security and tell you how to assess your environment to see if it can withstand firmware attacks.

Let Connection Secure Your Business with Microsoft Copilot for Security
When adopting generative AI, organizations must prioritize ethical and privacy standards and prepare IT infrastructure for deployment. Microsoft Copilot for Security, combined with Connection’s expertise, enables fast, efficient, and effective security operations.
Microsoft Copilot for Security Technical Readiness Assessment
Copilot for Security uses advanced AI to boost cybersecurity with real-time threat detection and automated response. Connection’s technical readiness assessment ensures your infrastructure is prepared to integrate Copilot, identifying gaps and recommending improvements for optimal protection.HP Print
HP Wolf Security
Experiences to Meet You Where and How You Work
HP Wolf Security for printers offers robust, hardware-enforced protection for businesses of all sizes. With secure boot, self-healing firmware, and fleet-wide compliance tools, HP safeguards sensitive data from endpoint threats. Small businesses benefit from simplified setup, cloud-based management, and scalable security—making enterprise-grade print protection accessible and affordable.
HP Security Manager
Grow Your Business the Secure Way
HP Security Manager delivers automated, policy-based print security across your fleet. Instantly secure new devices, streamline compliance, and simplify certificate management—helping businesses stay protected and productive.
HP Advance
Transform Digital Processes with a Complete, Flexible Solution
HP Advance streamlines document management with centralized control, secure authentication, encrypted pull printing, and flexible modules. Enhance efficiency, protect data, and simplify workflows with scalable, integrated HP Wolf Security features.Cisco
Cisco Secure Endpoint
Discover how Cisco Secure Endpoint delivers unified prevention, detection, and response with cloud-based analytics, advanced threat hunting, and machine learning—protecting every device against evolving cyber threats.

Cisco Security Suites
A New Era in Security
Discover how Cisco Security Suites deliver end-to-end, AI-powered protection for users, clouds, and networks. Built on Zero Trust, these integrated solutions simplify security, accelerate response, and scale with your business needs.
XDR Buying Guide
Navigate the Extended Detection and Response Market Like a Pro
Explore how Cisco XDR unifies multi-vendor security, automates threat detection and response, and streamlines analyst workflows—delivering comprehensive, AI-powered protection and resilience for today’s complex business environments.Modern Endpoint Protection Resources
Extended Detection and Response
Extended Detection and Response (XDR) empowers organizations to defend against modern cyber threats by integrating security across endpoints, identities, email, network, and cloud. XDR streamlines detection, reduces alert fatigue, and automates response, enabling lean IT teams to act quickly and efficiently. This unified approach delivers stronger protection, improved compliance, and better outcomes for businesses of all sizes.Secure Access Service Edge (SASE) and Zero Trust
SASE and Zero Trust modernize endpoint security by verifying every user and device before granting access. SASE delivers cloud-based protection and connectivity, while Zero Trust enforces strict, identity-driven controls—reducing risk, improving visibility, and ensuring secure access for endpoints across distributed environments.Endpoint Security in the Age of AI and Hybrid Work
Endpoint security is evolving to meet the demands of AI-driven threats and hybrid work environments. Organizations must protect diverse devices, including laptops, tablets, smartphones, and IoT, across both remote and office settings. Layered defenses, starting with hardware safeguards and extending through software and cloud protections, reduce risk, improve visibility, and unify protection to secure every endpoint consistently.Connection Community
Securing the Edge at Scale: What You Need to...
As enterprises race to embrace edge computing to drive agility, speed, and real-time intelligence, they’re also exposing a troubling reality:... Read More
Data Security and Compliance: Strengthening...
Data security is a critical priority for everyone, especially those who manage sensitive information across a variety of workstreams within... Read More
TechSperience Episode 137: Quantum Computing...
Quantum computing represents a significant shift in computational power, offering both opportunities and challenges for securing sensitive data. Join the... Read More
Navigating the Transition from Windows 10 to...
As the end of support for Windows 10 approaches, IT professionals are gearing up for the transition to Windows 11... Read More
Apple’s Commitment to Security: A Deep...
I’ve always been intrigued by Apple’s commitment to creating a seamless user experience while prioritizing advanced security measures. In this... Read More







