This website stores cookies on your computer.
These cookies are used to collect information about how you interact with our website and allow us to remember you. We use this information in order to improve and customize your browsing experience and for analytics and metrics about our visitors both on this website and other media. To find out more about the cookies we use, see our Privacy Policy.
Meet the HP EliteBoard G1a Next Gen AI PC. Pre-order Today!
Extended Detection and Response (XDR)
From Point Solutions to Unified Defense: Why XDR Matters Now
Why XDR, and Why Now?
Hybrid work, cloud adoption, SaaS sprawl, and AI-enabled threats are transforming the way attacks unfold. Adversaries now combine phishing, identity abuse, and cloud pivots within hours—often across multiple tools and teams. Meanwhile, lean IT groups must defend flexible cloud architecture and a growing identity surface with limited staff.IBM’s Cost of a Data Breach Report puts the global average breach cost at $4.4M—down 9% from 2024—due to faster detection and containment. However, the financial impact is still significant, and the stakes remain high.
While traditional point solutions—such as endpoint antivirus, firewalls, and log-centric Security Information and Event Management (SIEM) systems—excel in their respective domains, they still leave visibility gaps and produce uncorrelated alerts for teams to reconcile. For IT teams, that means more time spent stitching together signals and less time stopping threats.
Extended Detection and Response (XDR) changes the equation by adding a unifying operating layer across endpoints, identities, email, network, and cloud. This gives teams the ability to detect threats sooner and respond faster with optimized cybersecurity services.
The average cost of a data breach is $4.4M.1


What Is Extended Detection and Response?
Think of XDR as your security team’s way to extend detection and response across endpoints, identities, email, network, and cloud by pulling signals into one place and coordinating consistent responses. The outcome is clearer visibility, fewer duplicate alerts, and faster, more effective containment.Why Legacy Tools Create Silos
Traditional point solutions can only view part of the picture, producing disconnected alerts that analysts must manually piece together. This siloed approach is a big driver of alert fatigue. In fact, a Forrester-backed benchmark found that 61% of security teams are overwhelmed by too many threat-intel feeds, while 60% cite a shortage of skilled analysts. Together, these challenges slow response and increase risk.XDR solves this by unifying signals across technology touchpoints—helping teams proactively cut through noise, reduce duplication, and execute decisively.
Where EDR, SIEM, and MDR Fall Short
While traditional tools perform important work in specific threat vectors, none of them offer the unified, cross-domain coverage that XDR provides.
- EDR: While it’s excellent at host-level behavior and containment on the device itself, EDR doesn’t naturally follow an attack as it hops from a phish to an OAuth grant to a cloud workload. Telemetry is often vendor‑specific JSON with fields that don’t line up with your email or identity tools, so stitching the story together is slow.
- SIEM: Even as it’s valuable for centralizing logs and meeting compliance needs, SIEM sends data in different formats (syslog, JSON, proprietary exports) and requires ongoing parsing, tuning, and manual pivoting. When teams are short-staffed and overwhelmed by too many feeds, correlation queues grow—and containment slows.
- MDR: Though it adds round-the-clock analyst coverage, MDR lacks a shared incident model across tools, causing teams to lose time jumping between consoles to take action.
The XDR Advantage
Extended Detection and Response closes the gaps that single-purpose tools leave behind by linking activity across devices, users, email, network, and cloud into one coordinated story.
- Single incident narrative: This one storyline spans users, devices, email, network, and cloud, so security, IT, and compliance work from the same facts and decisions move faster.
- Faster detection and response: Analytics connect related events and highlight what matters sooner, and then trigger playbooks to isolate devices, revoke tokens, or force password resets. You spend less time triaging and more time containing.
- Reduced alert fatigue: Duplicates are grouped into a single case, and noisy detections are suppressed with context, so analysts review one incident instead of dozens of alerts. This reduces burnout and keeps attention on actions that lower risk.
XDR Helps Where Security Teams Struggle Most
61%
of teams are overwhelmed by too many intel feeds2
60%
of teams say they lack skilled analysts2
XDR consolidates alerts and automates routine tasks, reducing pressure on teams.
XDR’s Core Capabilities
Smaller or short-staffed teams buried in alerts can use Extended Detection and Response to finally see what’s important and act before issues escalate. By unifying detection and response across multiple domains, XDR shifts security teams from reactive firefighting to proactive control. For security leaders evaluating XDR, these are the features that deliver the most impact:
Many XDR solutions, including Microsoft Defender XDR and Sentinel, deliver these capabilities out of the box. Connection’s certified engineers help organizations design, implement, and manage these tools—and can integrate them with existing investments in platforms like CrowdStrike, Cisco, or Palo Alto Networks to maximize ROI.
Attackers don’t discriminate based on company size. Whether you’re a 200-person manufacturer or a 2,000-person healthcare provider, adversaries use enterprise-grade tactics like phishing, credential theft, and lateral movement to exploit any gap they find. Unfortunately, smaller and midmarket organizations often face these attacks with fewer people, tighter budgets, and a patchwork of legacy tools. That mismatch creates pressure on IT teams who are already stretched thin.
Extended Detection and Response helps filter out distractions by streamlining investigations and providing enterprise-grade defenses without enterprise-grade headcount.
XDR unifies detection and response across multiple domains, helping teams shift from damage control to proactive threat detection.
Why SMB and Midmarket Organizations Need XDR
Attackers don’t discriminate based on company size. Whether you’re a 200-person manufacturer or a 2,000-person healthcare provider, adversaries use enterprise-grade tactics like phishing, credential theft, and lateral movement to exploit any gap they find. Unfortunately, smaller and midmarket organizations often face these attacks with fewer people, tighter budgets, and a patchwork of legacy tools. That mismatch creates pressure on IT teams who are already stretched thin. Extended Detection and Response helps filter out distractions by streamlining investigations and providing enterprise-grade defenses without enterprise-grade headcount.
- Enterprise-level threats vs. smaller teams
Most SMB and midmarket IT groups juggle multiple feeds, such as EDR alerts, firewall logs, and email notifications, but don’t have enough analysts to connect them. The result is slower detection and longer dwell time for attackers. XDR levels the playing field by consolidating signals from endpoint, identity, email, cloud, and network into a single incident view, then automating routine triage so analysts can focus on what matters. - Compliance pressure
Whether it’s HIPAA in healthcare, PCI in retail, or growing demands from cyber-insurers, SMBs and midmarket companies face the same scrutiny as enterprises when it comes to proving security controls. But with smaller teams, documenting evidence can feel like another full-time job. XDR simplifies this by maintaining case histories, generating consistent response records, and providing unified reporting dashboards. Instead of scrambling at audit time, teams can “show their work” with a few clicks. - Budget and staffing constraints
The reality is that most midmarket organizations recognize the risk but struggle to invest at the level they’d like. CrowdStrike found that 93% of SMBs are aware of cyber risk, yet only 36% invest in new tools and just 11% use AI-driven defenses. For lean IT groups, adding headcount isn’t always an option. XDR helps extend capacity by embedding AI correlation, guided playbooks, and automated containment into daily operations. The result: more security outcomes without requiring more staff.
SMBs Recognize the Risk—But Struggle to Respond
93%
aware of cyber risk3
36%
invest in new tools3
11%
use AI-driven security3
XDR Adoption Business Outcomes
Security tools only matter if they deliver tangible results. For IT and business leaders alike, the value of Extended Detection and Response comes from translating faster detection and coordinated response into outcomes that reduce risk, improve continuity, and maximize the return on existing security investments.- Faster MTTD/MTTR (Mean Time to Detect/Res)
AI-driven correlation and automated containment mean threats are detected and contained before they escalate. For example, a regional healthcare provider may be able to cut investigation time in half by using XDR to automatically quarantine suspicious emails and flag risky sign-ins, helping them meet HIPAA reporting requirements without adding staff. - Lower breach and ransomware risk
By catching anomalies earlier, XDR limits lateral movement and reduces the blast radius of attacks. A multi-plant manufacturer, for example, could use XDR to link identity abuse to endpoint persistence, isolating compromised devices before ransomware spread across operations, which would protect uptime on the shop floor. - Higher ROI on existing tools
Most midmarket organizations already own multiple security platforms, but they operate in silos. XDR connects endpoint, identity, email, cloud, and SIEM investments to produce better outcomes without new licensing costs. For instance, a retailer managing dozens of stores and an e-commerce site could use XDR to unify monitoring across POS, email, and cloud systems, enabling them to cut false positives and improve PCI reporting efficiency. - Better alignment to continuity and compliance
Auditors and insurers increasingly demand proof of detection and response capabilities. XDR creates unified playbooks, telemetry, and case histories to simplify evidence gathering. That means smoother HIPAA, PCI, or cyber-insurer reviews and fewer fire drills for IT staff. - Enterprise-grade results without enterprise-grade headcount
Automation and guided investigations help smaller teams scale up without new hires. Whether it’s a hospital IT department of three people or a lean retail security team, XDR can give them the same capabilities large enterprises enjoy, but without the cost.
Getting Started with XDR
Extended Detection and Response adoption doesn’t have to mean ripping and replacing everything you have today. The most successful deployments start with a baseline: where are your gaps, what do auditors and insurers expect, and which integrations will deliver the fastest wins? By taking a phased approach, you’ll build confidence in the technology and ensure your team gets value from day one.
Step 1: Assess your gaps
Start by mapping where your alerts come from today—endpoints, identity systems, email gateways, cloud apps, and network tools. Which of these signals are already centralized, and which live in silos? Look closely at where investigations tend to stall (e.g., when identity data doesn’t connect to endpoint alerts). A gap analysis gives you the clearest picture of where XDR can add the most value.
Step 2: Map to compliance and insurance
Most frameworks (HIPAA, PCI, NIST) and cyber-insurers want to see evidence that you can detect, investigate, and contain incidents. Make a checklist of the artifacts you’ll need: case notes, timelines of response actions, audit logs, and proof of containment. Aligning XDR capabilities to these requirements early means you’re not scrambling during an audit or renewal conversation.
Step 3: Identify Integrations
Not every integration has an equal impact. Prioritize the “big four” planes first: endpoint, identity, email, and cloud. These generate the highest-value signals for detecting credential abuse, phishing, or lateral movement. Over time, add in network telemetry, OT systems, and third-party threat intelligence. Each layer you connect makes your incident view more complete and your response faster.
Step 4: Partner with a Trusted IT Advisor
Finally, XDR works best when it’s aligned with your broader IT and security strategy. Many organizations choose to work with a partner to help design, implement, and fine-tune their XDR deployment. A good partner will ensure integrations are configured properly, help you operationalize automated playbooks, and provide ongoing support so your team can focus on higher-value work.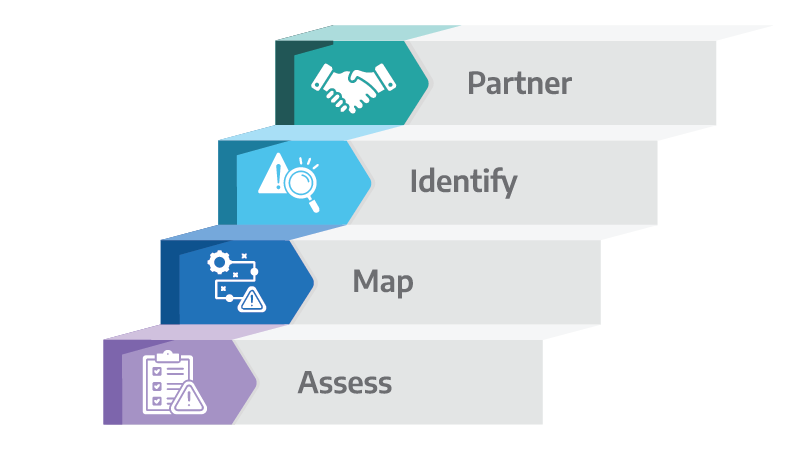
Signs Your Team Needs XDR
If any of these sound familiar, your security operations may be ready for XDR:Do you have visibility gaps across endpoints, identities, cloud, email, and network?
Do alerts outpace your team’s capacity?
Are manual handoffs between tools delaying containment?
Would automated containment reduce after-hours risk?
Take Control and Get Stronger Security
Today’s attackers move fast and can chain phishing, identity abuse, and cloud pivots within hours. At the same time, lean IT teams are buried in alerts and stretched thin on staff. It’s no surprise that 61% of security teams report being overwhelmed by too many intel feeds, while IBM puts the average global breach cost at $4.44M in 2025.XDR offers a practical way forward: filtering irrelevant alerts, unifying signals, and orchestrating consistent response across endpoint, identity, email, network, and cloud. For SMB and midmarket organizations, that means stronger defenses, simplified compliance, and enterprise-grade results—all without enterprise-grade headcount.
Ready to Explore What’s Next?
Start with a Security Assessment or explore Microsoft Security Services and Defender XDR Implementation Services with your Connection team.
Connection Microsoft Defender XDR Implementation Services
Let Our Experts Build Your United Defense
In today’s digital landscape, cybersecurity threats are becoming increasingly sophisticated and pervasive. Microsoft Defender eXtended Detection and Response (XDR) is a cloud-native platform designed to provide comprehensive protection by collecting, correlating, and analyzing security data from various sources, including endpoints, networks, applications, cloud workloads, and identity infrastructure.1 IBM. Cost of a Data Breach Report. 2023.
2 Forrester. Threat Intelligence Benchmark: Stop Reacting; Start Anticipating. July 2025.
3 Business Wire. CrowdStrike Unveils State of SMB Cybersecurity Report: High Awareness, Lagging Protection. May 2025.
2 Forrester. Threat Intelligence Benchmark: Stop Reacting; Start Anticipating. July 2025.
3 Business Wire. CrowdStrike Unveils State of SMB Cybersecurity Report: High Awareness, Lagging Protection. May 2025.