This website stores cookies on your computer.
These cookies are used to collect information about how you interact with our website and allow us to remember you. We use this information in order to improve and customize your browsing experience and for analytics and metrics about our visitors both on this website and other media. To find out more about the cookies we use, see our Privacy Policy.
SASE and Zero Trust
Building the Foundation for Future-ready Secure Networking
Why Secure Networking Needs a New Foundation
For decades, organizations relied on perimeter-based security, the idea that if you build strong defenses around your network, everything inside will remain safe. That model worked when most users, applications, and data lived within the same physical environment. But today, the workplace has fundamentally changed.Cloud adoption, hybrid work models, and the explosion of mobile devices have stretched the network far beyond the traditional perimeter. Employees connect from anywhere, critical applications live in multiple clouds, and sensitive data moves constantly between environments. This expanded attack surface has made it easier for adversaries to find and exploit weak points, while making it harder for security teams to enforce consistent policies.
Modern IT and security leaders need a more flexible, adaptive, and identity-aware approach to keep pace with this shift. That’s where two transformative frameworks come into play: Secure Access Service Edge (SASE) and Zero Trust. Rather than relying on a fixed boundary, these strategies emphasize verifying every user, device, and connection, no matter where they originate.
Individually, SASE and Zero Trust offer powerful security and networking benefits. Together, they form the backbone of the future of secure networking, enabling organizations to protect distributed environments while supporting agility, productivity, and growth.
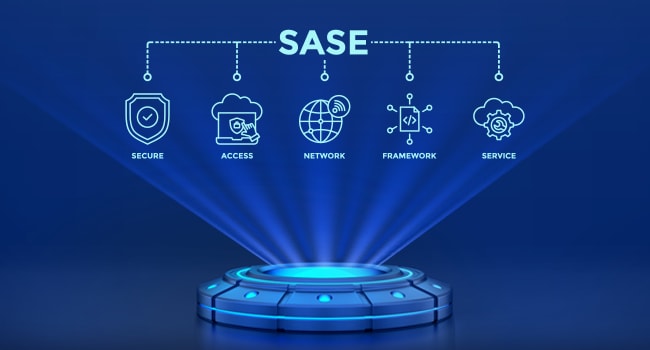
What Is Secure Access Service Edge (SASE)?
As cloud adoption accelerates and workforces become more distributed, organizations need a security model that can keep up. SASE is a modern, cloud-delivered architecture that brings networking and security together into a single, unified framework. Instead of managing separate point solutions across multiple environments, SASE consolidates critical capabilities and delivers them closer to the user, wherever that user is.Core components of SASE include:
- Software-defined Wide Area Networking (SD-WAN): Enables secure, high-performance connectivity between users, applications, and cloud services.
- Cloud Access Security Broker (CASB): Provides visibility and control over cloud application usage.
- Firewall as a Service (FWaaS): Extends next-generation firewall capabilities to the cloud, reducing the need for on-premises appliances.
- Secure Web Gateway (SWG): Protects users from Internet-based threats by filtering traffic at the edge.
- Zero Trust Network Access (ZTNA): Replaces traditional VPNs with identity-based, context-aware access controls.
Key benefits of SASE include:
- Simplified Management: Centralized control over security and networking policies.
- Scalability: Cloud delivery enables flexible support for remote workers, branch offices, and growing workloads.
- Consistent Security: Policies can be enforced uniformly across all locations and devices.
SASE doesn’t just protect the network perimeter. It eliminates the need for a fixed perimeter altogether, ensuring secure, reliable access to critical resources no matter where users are located.
What Is Zero Trust Security?
Where SASE focuses on how security and networking are delivered, Zero Trust defines how access is granted and enforced. At its core, Zero Trust is a security philosophy built on one simple idea: “never trust, always verify.”Instead of assuming that users or devices inside the network are safe, Zero Trust treats every connection as untrusted until proven otherwise. Access is granted based on identity, device health, and contextual signals, not location.
According to the Cisco Zero Trust Outcomes Report, more than 86% of organizations have already begun moving to Zero Trust, though only 2% have achieved full maturity across all pillars. This demonstrates how central Zero Trust has become to modern security strategies, even as many teams are still on the journey toward complete implementation.
Core principles of Zero Trust include:
- Least privilege: Users and devices get only the access they need to perform their roles.
- Continuous authentication and monitoring: Trust is evaluated dynamically, not just at login.
- Microsegmentation: Breaking the network into smaller, controlled zones to limit lateral movement if a breach occurs.
Key benefits of Zero Trust include:
- Reduced attack surface: Limits how far threats can spread inside the network.
- Stronger breach resilience: Even if attackers get in, they have fewer pathways to exploit.
- Improved visibility: Centralized monitoring provides a clearer view of users, devices, and access patterns.

A Practical Guide to Zero Trust Implementation in Multicloud Environments
This guide outlines a strategic, step-by-step approach to implementing Zero Trust in multicloud environments. It explains core principles, official frameworks from NIST and CISA, maturity models, and practical deployment strategies. Emphasis is placed on identity, automation, risk-based prioritization, and partnering with experts to navigate complex architectures and ensure cyber resilience.Why SASE and Zero Trust Are Better Together
Many organizations approach modern security by choosing between new frameworks. But SASE and Zero Trust are not competing models. They are complementary strategies that address different—but equally critical—aspects of secure networking in a cloud-first world.Both approaches share a common goal: enabling secure, seamless access to applications and data based on identity, not location. As organizations adopt multicloud infrastructure and support distributed workforces, the network perimeter no longer defines trust. Instead, trust must be verified dynamically, and access must be delivered securely from anywhere.
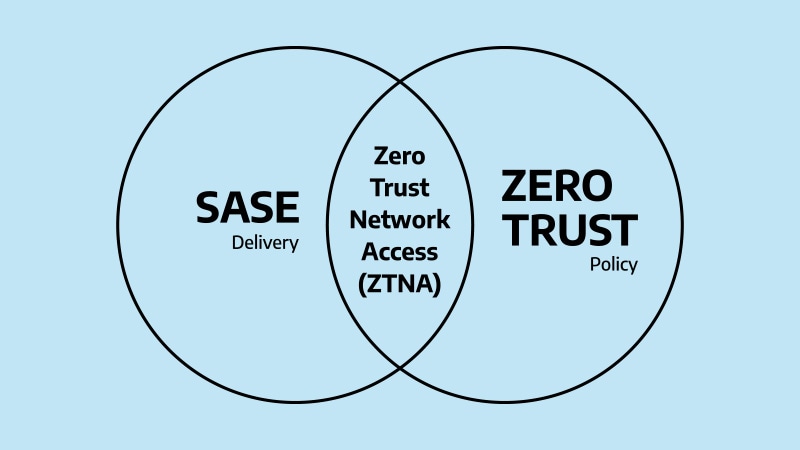
The key difference lies in their roles:
- SASE is the delivery architecture. It’s how security and connectivity are provided through a cloud-native platform that brings networking and security functions closer to users.
- Zero Trust is the security philosophy. It defines what gets access, under what conditions, and why. Its principles guide identity verification, access control, and continuous monitoring.
3 Practical Use Cases for SASE + Zero Trust
How SASE and Zero Trust Work Together
The true power of SASE and Zero Trust emerges when they work in tandem. At the core of both frameworks is a shared foundation: identity and access management (IAM)—the policies and technologies that ensure the right users (and devices) have the right level of access to the right resources. Instead of securing only the network perimeter, modern security models center on verifying who the user is, what device they’re on, and what level of access they should have every time.Building on that foundation, Zero Trust Network Access (ZTNA) extends IAM principles to network and application access. ZTNA, which is a core component of SASE, replaces the broad, implicit trust of traditional VPNs with policy-driven, identity-based access controls. Rather than granting access to an entire network, users are given the minimum required access to specific applications or resources. This dramatically reduces the attack surface and limits the blast radius if a breach occurs.
SASE operationalizes these Zero Trust principles by delivering them consistently across distributed environments. Whether users connect from home, a branch office, or a mobile device, the same security policies apply without requiring complex configurations or on-premises infrastructure.
3 Real-world Scenarios Where SASE and Zero Trust Intersect
Replacing VPNs
ZTNA delivers secure, user-centric access without the bottlenecks and risks of traditional VPNs. Through SASE, those same ZTNA policies are enforced consistently across remote users, branches, and cloud edges, eliminating the need for multiple point solutions or on-premises gateways.
Securing SaaS Adoption
Centralized policy enforcement helps organizations protect sensitive data across multiple cloud platforms and SaaS applications. With SASE, those access and inspection controls live in the cloud, ensuring every connection is authenticated, encrypted, and inspected using the same Zero Trust rules.
Enabling BYOD Strategies
Identity-based access and continuous verification ensure that unmanaged devices can be used safely without exposing the network to unnecessary risk. SASE adds the network and edge context, extending that verification to the traffic itself—so even personal devices route through secure, policy-driven access paths without requiring a local agent or VPN.
The Business Benefits of SASE and Zero Trust Integration
As organizations modernize their security strategies, the combination of SASE and Zero Trust offers more than just technical advantages. It drives measurable business value, including centralized role-based access control, microsegmentation, just-in-time access, and identity-based controls. By unifying delivery and policy under a single, identity-centric model, IT leaders can simplify their security ecosystem, improve resilience, and enhance user experiences without sacrificing control.
Reduced Complexity and Tool Sprawl
Many organizations still rely on a patchwork of legacy tools, each handling a different aspect of networking or security. This fragmented approach increases operational overhead, creates blind spots, and slows response times. SASE and Zero Trust integration reduces complexity by consolidating functions, from access control to traffic inspection, into a single, cloud-delivered framework.
Industry research underscores that streamlined IT operations and simplified management are among the most common outcomes of SASE adoption. This approach enables organizations to reduce the number of vendors, to streamline deployments, and to ease administrative overhead as network and security functions converge.
Industry research underscores that streamlined IT operations and simplified management are among the most common outcomes of SASE adoption. This approach enables organizations to reduce the number of vendors, to streamline deployments, and to ease administrative overhead as network and security functions converge.
Stronger Defense Against Modern Threats
Today’s attackers exploit identity, endpoint, and third-party vulnerabilities, making static perimeter defenses ineffective. By combining SASE’s centralized enforcement with Zero Trust’s “never trust, always verify” approach, organizations build stronger defenses against ransomware, insider threats, and supply chain risks.
Research shows that SASE and Zero Trust help shrink the attack surface and improve containment through identity-based access control and microsegmentation. Studies also show that reduced risk and improved security posture are top benefits of SASE strategies.
Research shows that SASE and Zero Trust help shrink the attack surface and improve containment through identity-based access control and microsegmentation. Studies also show that reduced risk and improved security posture are top benefits of SASE strategies.
Improved User Experience
Security shouldn’t come at the expense of productivity. ZTNA within SASE frameworks enables fast, secure access to applications without the friction of clunky VPN logins or latency issues. Employees get a seamless experience whether they’re in the office, at home, or on the go.
Studies highlight improved user experience, simplified access, and VPN removal as key outcomes of SASE adoption, leading to better end-user satisfaction and reduced IT support overhead. Additional findings note that performance and accessibility improve when security is centralized and cloud-delivered.
Studies highlight improved user experience, simplified access, and VPN removal as key outcomes of SASE adoption, leading to better end-user satisfaction and reduced IT support overhead. Additional findings note that performance and accessibility improve when security is centralized and cloud-delivered.
Compliance and Regulatory Alignment
Regulated industries face growing pressure to demonstrate control over access and data flows. SASE and Zero Trust make it easier to enforce consistent, auditable security policies across all users and environments. These frameworks help organizations align with regulatory requirements, such as HIPAA, PCI DSS, and GDPR.
Tangible ROI Through Simplified Operations
Beyond security gains, consolidation delivers cost and resource efficiencies. Fewer licenses, simpler integrations, and centralized management reduce administrative burden, free up IT resources, and support long-term scalability.
One study finds that organizations adopting SASE and Zero Trust achieve cost savings tied to simplified security operations and reduced risk exposure, while another study highlights operational efficiency and lower overhead as key drivers of SASE investment. Together, these frameworks help IT teams do more with less while supporting business agility.
One study finds that organizations adopting SASE and Zero Trust achieve cost savings tied to simplified security operations and reduced risk exposure, while another study highlights operational efficiency and lower overhead as key drivers of SASE investment. Together, these frameworks help IT teams do more with less while supporting business agility.
How to Implement SASE and Zero Trust in Your Organization
Moving to a SASE and Zero Trust model doesn’t require a complete overhaul on day one. The most successful organizations approach the transition methodically, building on their existing infrastructure, layering in modern capabilities, and refining over time. Here’s a practical roadmap to implementation.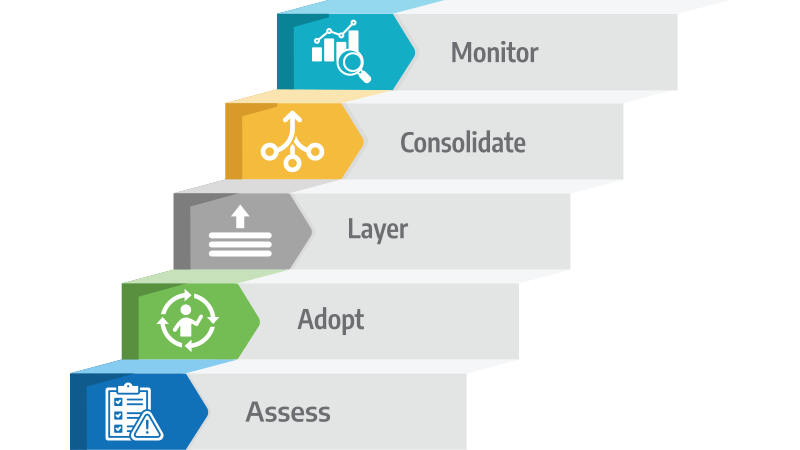
Step 1: Assess Your Current Environment
A successful strategy starts with visibility. Evaluate your legacy VPN architecture, identity and access management systems, SaaS footprint, and network topology. Identifying where users, devices, and applications live, and how they connect. This helps you uncover gaps and prioritize areas for modernization.
Step 2: Adopt Zero Trust Principles First
Before deploying new tools, establish the foundation of Zero Trust:✔ Shift from perimeter-based to identity-centric security.
✔ Define clear access policies based on least privilege.
✔ Implement continuous authentication and monitoring to verify trust dynamically.
Step 3: Layer in SASE Components Incrementally
Instead of a “big bang” rollout, adopt SASE in phases. Start with components that provide the biggest impact. For many organizations, that’s ZTNA to replace legacy VPNs or SD-WAN to improve connectivity and performance. Over time, expand to include Cloud Access Security Broker (CASB), Secure Web Gateway (SWG), and Firewall as a Service (FWaaS) for full coverage.
Step 4: Consolidate Vendors and Solutions
Tool sprawl can undermine even the best security strategies. Consolidating point solutions into a single, cloud-delivered SASE platform streamlines management, reduces costs, and improves consistency in policy enforcement.
Step 5: Use Monitoring and Analytics to Refine Over Time
SASE and Zero Trust are not set-and-forget frameworks. Continuous monitoring, analytics, and threat intelligence help refine policies, optimize performance, and adapt to evolving business needs.
Common Pitfalls to Avoid
✘ Piecemeal deployments: Deploying disconnected tools without a unifying strategy can increase complexity instead of reducing it.
✘ Ignoring user experience: Security controls should enhance, not hinder, productivity. Seamless access drives adoption and reduces support burden.
Secure the Future with SASE and Zero Trust
The future of secure networking isn’t about choosing between SASE and Zero Trust. It’s about combining their strengths. SASE provides the delivery architecture. Zero Trust defines the security philosophy. Together, they create a unified, identity-centric security framework that simplifies operations, strengthens defenses, and prepares organizations for what’s next.Companies that embrace this integrated approach are better positioned to reduce complexity, improve resilience, and enable secure access anywhere, for any user or device. By aligning strategy, technology, and policy, IT leaders can build a flexible foundation that supports hybrid work, cloud adoption, and evolving compliance requirements.
Connection can help guide that journey. Our team works with organizations to:
✔ Conduct security assessments to identify gaps and opportunities.
✔ Facilitate strategic planning workshops to chart the path forward.
✔ Provide next-step guidance for building and optimizing modern secure networking architectures.
Work with our experts to assess your environment, shape a secure networking strategy, and simplify your path to SASE and Zero Trust.
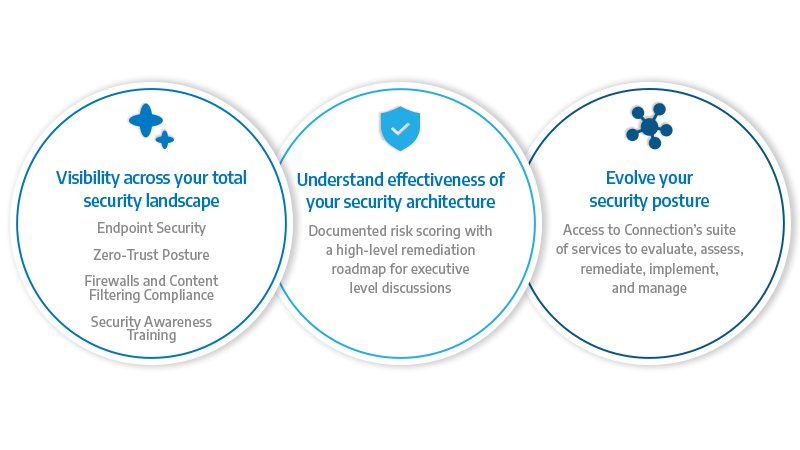
Strategic Security Evaluation
Fully documenting your security posture is an important step when trying to effectively govern risk. Our Strategic Security Evaluation offers a comprehensive overview—facilitated by expert technical resources—of your security stack across endpoints, networks, data, cloud, and compliance. This service provides clear guidance on your security capabilities and a roadmap to help you close defensive risk. Get the coverage your enterprise deserves.