This website stores cookies on your computer.
These cookies are used to collect information about how you interact with our website and allow us to remember you. We use this information in order to improve and customize your browsing experience and for analytics and metrics about our visitors both on this website and other media. To find out more about the cookies we use, see our Privacy Policy.
What Promising Advancements or Innovations in Endpoint Protection Technology Should Businesses Be Aware of?
Get the Latest on Endpoint Protection Technology Advancements from the Experts
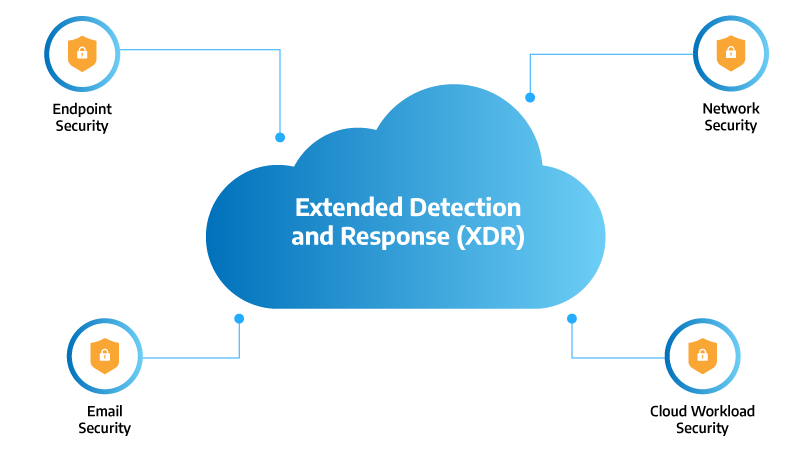
There’s also been a big leap forward in AI- and ML-powered threat detection, which helps identify unusual behavior and stop zero-day attacks before they cause damage. Many modern platforms can now detect suspicious activity even if it doesn’t match a known malware signature, allowing for earlier intervention. Cloud-delivered endpoint protection is another major shift. It enables businesses to manage and update security policies across all devices, no matter where employees are working, without the need for on-premises infrastructure. Some tools also now include automated response capabilities, reducing the time it takes to contain threats once detected.
With remote work, BYOD policies, and distributed teams becoming the norm, innovations like these are helping businesses stay a step ahead without overwhelming their IT teams.
Get Endpoint Protection Help from the Experts
Managed and Monitored Security Services

