This website stores cookies on your computer.
These cookies are used to collect information about how you interact with our website and allow us to remember you. We use this information in order to improve and customize your browsing experience and for analytics and metrics about our visitors both on this website and other media. To find out more about the cookies we use, see our Privacy Policy.
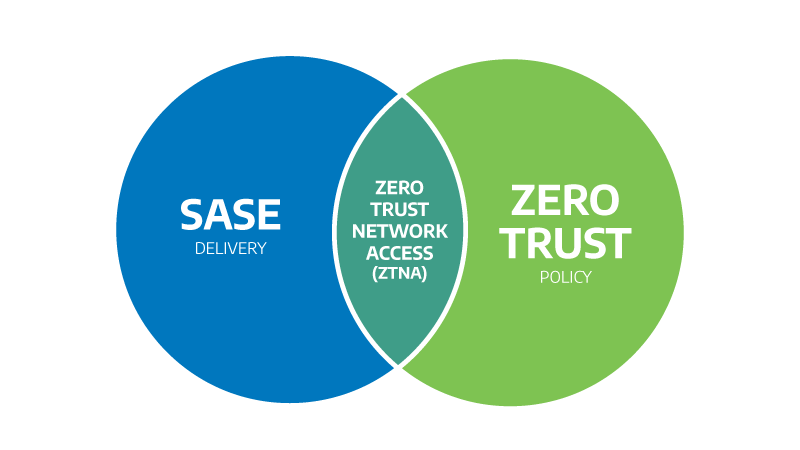
Zero Trust and SASE
A Practical Guide to Zero Trust with SASE Delivery
Enterprise networks have evolved beyond the walls of the data center. Applications live in public clouds, users work from anywhere, and the traditional perimeter has all but disappeared. This shift has created new opportunities for flexibility and collaboration, but it has also made data protection more complex.
The solution is not another perimeter; it is a new way of thinking about trust. Zero Trust Architecture (ZTA) and Secure Access Service Edge (SASE) together offer a framework that allows organizations to deliver secure access to users wherever they are. Zero Trust focuses on verifying every request, while SASE provides the distributed architecture to enforce those policies across networks and cloud environments.
According to Gartner, SASE has become a defining model for secure connectivity because it merges network performance and security into a single, cloud-delivered platform. At the same time, NIST SP 800-207—the U.S. government’s official Zero Trust Architecture framework—describes Zero Trust as an approach that continuously validates identity, context, and device health before granting access.
This guide explores how organizations can design and implement Zero Trust and SASE architectures that provide both security and agility. It covers the core components of each model, their integration points, and how automation and governance can turn these concepts into sustainable business practices.
The solution is not another perimeter; it is a new way of thinking about trust. Zero Trust Architecture (ZTA) and Secure Access Service Edge (SASE) together offer a framework that allows organizations to deliver secure access to users wherever they are. Zero Trust focuses on verifying every request, while SASE provides the distributed architecture to enforce those policies across networks and cloud environments.
According to Gartner, SASE has become a defining model for secure connectivity because it merges network performance and security into a single, cloud-delivered platform. At the same time, NIST SP 800-207—the U.S. government’s official Zero Trust Architecture framework—describes Zero Trust as an approach that continuously validates identity, context, and device health before granting access.
This guide explores how organizations can design and implement Zero Trust and SASE architectures that provide both security and agility. It covers the core components of each model, their integration points, and how automation and governance can turn these concepts into sustainable business practices.
Core Components of Zero Trust and SASE Architecture
Identity-first Architecture
Identity is the foundation of Zero Trust. Every access decision begins with verifying who is requesting it and assessing the risk involved. Instead of assuming that a user inside the network is safe, modern security checks every request against identity, device posture, and context.A strong Identity and Access Management (IAM) framework centralizes these controls. It verifies users through Multifactor Authentication (MFA), monitors device compliance, and ensures that privileges match roles. Policies also account for context—such as time of access, geolocation, or whether a device connects from a managed or unmanaged network.
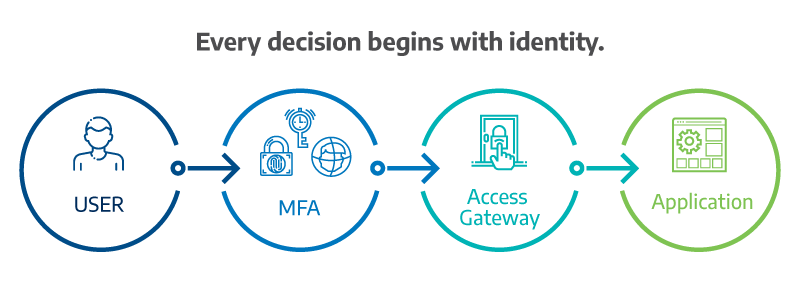
In practice, this means users working from personal laptops or public Wi-Fi may face additional checks before accessing sensitive systems. Microsoft’s Zero Trust Overview outlines this approach as a three-part model: verify explicitly, use least privilege, and assume breach.
Identity-first design not only protects against credential misuse but also simplifies user management. Once identity becomes the single source of truth, access can be controlled consistently across SaaS applications, internal systems, and cloud workloads.
Identity-first design not only protects against credential misuse but also simplifies user management. Once identity becomes the single source of truth, access can be controlled consistently across SaaS applications, internal systems, and cloud workloads.
Policy Decision and Enforcement
Zero Trust works through continuous, dynamic policy enforcement. Two primary components drive this: the Policy Decision Point (PDP) and the Policy Enforcement Point (PEP).The PDP gathers information about the user, device, and application, then evaluates whether access should be granted. It looks at variables such as role, device compliance, network location, and ongoing threat intelligence. The PEP then applies the decision directly within the traffic path—whether through a Zero Trust Network Access (ZTNA) gateway, Firewall-as-a-service, or Secure Web Gateway.
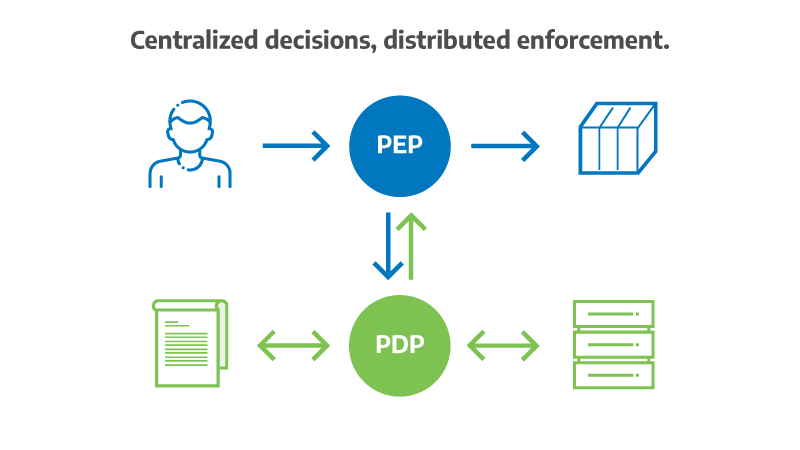
This structure, described in NIST SP 800-207, keeps enforcement close to the workload while ensuring that policy logic remains centralized.
For example, a finance analyst attempting to access an enterprise resource planning (ERP) system from an approved laptop in a corporate office may be granted immediate access. The same request from a personal tablet at home might trigger a step-up authentication or limited access session.
This adaptive enforcement reduces risk without impacting productivity. It also creates audit-ready logs of each decision, which are critical for compliance and forensics.
For example, a finance analyst attempting to access an enterprise resource planning (ERP) system from an approved laptop in a corporate office may be granted immediate access. The same request from a personal tablet at home might trigger a step-up authentication or limited access session.
This adaptive enforcement reduces risk without impacting productivity. It also creates audit-ready logs of each decision, which are critical for compliance and forensics.
Network and Security Convergence
Historically, network teams focused on performance while security teams focused on protection. With SASE, those two functions are combined into a unified, cloud-based architecture that delivers both.SASE integrates SD-WAN for optimized routing with security controls such as Secure Web Gateway (SWG), Cloud Access Security Broker (CASB), ZTNA, and Firewall-as-a-service (FWaaS). This convergence streamlines management, ensures consistent enforcement, and supports distributed users without the need for multiple on-premises appliances.
Organizations that adopt this approach benefit from simplified infrastructure and reduced operational overhead. Traffic flows directly to the Internet or cloud applications through the nearest point of presence, where policy is applied instantly. This reduces latency, minimizes backhauling costs, and keeps user experiences fast and reliable.
According to Gartner’s SASE overview, Secure Access Service Edge has become a defining model for secure connectivity because it merges network performance and security into a single, cloud-delivered platform. The related Gartner Security Service Edge (SSE) framework focuses specifically on the security capabilities—such as SWG, CASB, and ZTNA—that form the foundation of SASE architectures.
Microsegmentation and Workload Protection
While identity governs who gets in, microsegmentation controls what they can access once inside. This approach divides the environment into small, manageable zones, each with its own security rules.If an attacker breaches one area, microsegmentation limits lateral movement by requiring separate authentication for every zone. These zones might be divided by department, application type, or data classification level.
Implementing microsegmentation also supports compliance requirements. Regulations such as HIPAA and GDPR require organizations to restrict access to sensitive data and log who accesses it. By combining segmentation with identity-driven policies, organizations can demonstrate that controls are both technical and procedural.
NIST SP 800-207 highlights segmentation as essential to Zero Trust. When applied alongside SASE’s distributed enforcement, it becomes a core mechanism for limiting risk and protecting workloads across hybrid and multicloud environments.
Telemetry and Analytics
Zero Trust and SASE rely on visibility. Without continuous telemetry, organizations cannot validate whether policies are working or detect threats early.
Telemetry data includes authentication events, device compliance status, network activity, and application performance. By analyzing these signals in real time, organizations can identify patterns that indicate risk: such as unusual logins, abnormal data transfers, or system configuration changes.
Analytics engines now use machine learning to correlate this information across multiple domains. For example, a spike in failed logins from an unfamiliar location might automatically trigger step-up verification or alert the security team.
The CISA Zero Trust Maturity Model identifies continuous monitoring as a key maturity milestone. By feeding telemetry back into the policy engine, organizations can make data-driven adjustments that improve both security and performance.
Analytics engines now use machine learning to correlate this information across multiple domains. For example, a spike in failed logins from an unfamiliar location might automatically trigger step-up verification or alert the security team.
The CISA Zero Trust Maturity Model identifies continuous monitoring as a key maturity milestone. By feeding telemetry back into the policy engine, organizations can make data-driven adjustments that improve both security and performance.
The SASE Delivery Layer: Extending Zero Trust Across the Edge
SASE as the Enforcement Fabric
SASE provides the infrastructure that brings Zero Trust to life across distributed environments. It delivers policy enforcement through globally distributed points of presence (PoPs) that are located close to users and applications.
Each PoP acts as a secure access node that inspects traffic, applies policy, and connects users to the fastest, most reliable route. This design ensures consistent protection without forcing traffic to travel back through a central data center.
Cloud-native providers have shown how this architecture can scale globally while maintaining low latency and high performance.
Cloud-native Edge Delivery
Cloud-native edge delivery enables scalability that traditional hardware cannot match. As organizations expand into new regions or shift workloads between providers, SASE’s distributed enforcement adapts automatically.
Instead of deploying physical appliances, IT teams connect users or offices to nearby PoPs through secure tunnels. Policies propagate globally within minutes, ensuring uniform protection and minimal downtime.
This approach not only simplifies deployment but also aligns with sustainability goals by reducing hardware footprints and power consumption, a growing consideration for IT leaders planning long-term infrastructure strategies.
Sustainability Spotlight
Cloud-native edge delivery reduces hardware waste and energy usage, aligning security modernization with ESG goals.
Integrating SD-WAN and the Security Service Edge
SASE’s value increases when SD-WAN and the Security Service Edge (SSE) operate together. SD-WAN manages network paths and ensures performance, while SSE provides the inspection and control layer. When these layers share a management interface, teams gain unified visibility into performance and security events. They can identify bottlenecks, apply consistent policies, and respond to incidents faster. Integration also reduces overlap between tools and helps align network and security priorities.
ZTNA as the Link Between Policy and Delivery
ZTNA is where Zero Trust and SASE converge. It authenticates users and devices at every connection and allows access only to specific applications or services. Unlike VPNs, it does not expose entire networks.
ZTNA continuously validates the session using identity, device health, and behavioral analytics. If risk increases, it can terminate access instantly. This principle of “never trust, always verify” ensures that permissions remain valid only for the context in which they were granted.
Design Considerations
Creating a SASE-enabled Zero Trust environment requires thoughtful design. Enforcement points should be located near users to minimize latency, and policies must be synchronized globally.
Reliability is another priority. Build redundancy into PoPs, routing paths, and policy engines to ensure uptime even during outages. Choose vendors that support open standards such as SAML, OAuth, and SCIM for identity integration, along with APIs for automation and reporting.
Finally, consider user experience as part of the architecture. Security that slows productivity can lead to workarounds, while well-designed Zero Trust and SASE frameworks can actually enhance performance through optimized routing and simplified access.
Designing a Unified Zero Trust and SASE Architecture
Identity as the Policy Anchor
In a unified design, identity replaces the network as the anchor of access control. Policies define what users can do based on who they are, their device health, and the sensitivity of the resource.
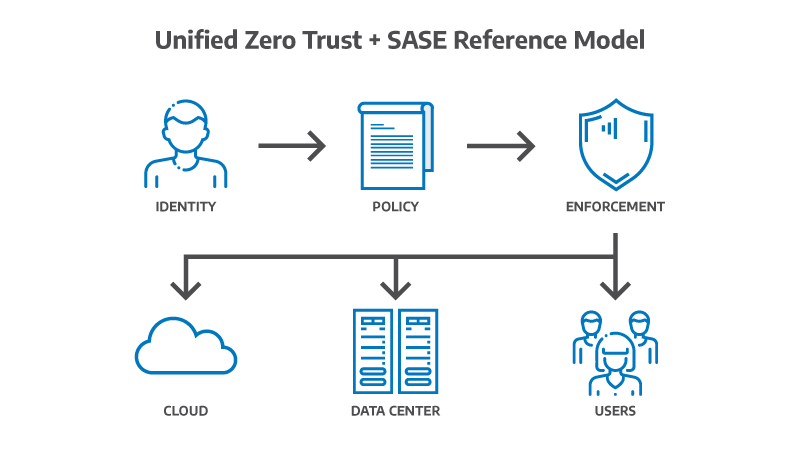
This structure simplifies operations by consolidating policies under a single engine that governs both internal and external access. It also provides a clear audit trail showing who accessed what, when, and from where, a key advantage during compliance reviews.
Defining these relationships ensures there are no blind spots. It also helps teams visualize how each policy affects users and workloads, which supports both troubleshooting and optimization.
Mapping Policies to Enforcement
To make policies actionable, they must connect directly to enforcement points. A rule that grants engineers access to development environments while blocking data uploads to personal storage may map to ZTNA and CASB controls, while a broader policy restricting Internet content applies through SWG.Defining these relationships ensures there are no blind spots. It also helps teams visualize how each policy affects users and workloads, which supports both troubleshooting and optimization.
Integration Models
Integration depends on an organization’s infrastructure maturity. In cloud-first models, applications live primarily in SaaS or IaaS environments. Users connect through SASE PoPs, where SWG and CASB secure Web and cloud traffic, and ZTNA manages private application access.
A hybrid approach supports both cloud and on-prem systems. SD-WAN connects branch offices to SASE PoPs for consistent policy enforcement, while microsegmentation protects internal networks.
For multicloud operations, identity and policy engines must function across providers. Centralized logging and telemetry collection maintain a unified view, and common tagging standards help align applications and data across environments.
Each model benefits from automation that keeps configurations synchronized and responsive to change.
Blueprint Example: ZTNA and SD-WAN for Dynamic Access
A combined ZTNA and SD-WAN design demonstrates how Zero Trust and SASE reinforce each other.
The identity provider authenticates users and verifies device compliance. The policy engine defines allowable actions and risk thresholds. SD-WAN determines the fastest route between endpoints, and ZTNA enforces application-level access along that path.
Telemetry from both systems feeds into analytics dashboards, revealing usage patterns and potential risks. If the system detects unusual behavior, such as large data transfers from a privileged account, it can trigger step-up verification or session termination.
This continuous feedback loop keeps security aligned with user activity and business priorities.
ZTNA and SD-WAN are most effective when identity, performance, and automation work together. Continuous telemetry turns this pairing into a self-adjusting system that aligns access and risk in real time.
Automating Secure Access
Automation brings consistency and scale to Zero Trust and SASE operations.
Policy as Code translates access rules into structured files that can be tested and version-controlled. Teams can review changes, simulate outcomes, and roll them out gradually. This reduces configuration errors and ensures policies stay aligned with corporate standards.
Infrastructure as Code (IaC) applies similar principles to deployment. Tools like Terraform and Ansible can create or update ZTNA gateways, configure routing rules, and maintain consistent setups across regions. As noted in Cisco’s Zero Trust guidance, codifying these processes reduces complexity and accelerates response to new threats.
When automation and analytics work together, they enable event-driven actions. For instance, a compromised device can trigger immediate isolation, or a new compliance requirement can deploy updated configurations across all enforcement points within minutes.
Governance, Compliance, and Measurement
Governance ensures at architecture improvements are measurable and sustainable. Frameworks such as NIST SP 800-207 and the CISA Zero Trust Maturity Model provide clear paths for assessing progress.
Regulatory frameworks, including ISO 27001, HIPAA, and GDPR, establish standards for protecting data and maintaining privacy. Mapping Zero Trust and SASE controls to these frameworks demonstrates compliance and simplifies audits.
Strong governance also depends on clear ownership. Role-based access control, least-privilege policies, and centralized logging ensure accountability. By tracking every access request and policy change, organizations can respond quickly to incidents and maintain transparency.
Measurement completes the cycle. Key indicators include policy consistency across PoPs, mean time to detect and respond (MTTD and MTTR), compliance readiness, and user experience metrics such as latency and connection reliability. Tracking these over time helps IT leaders quantify the value of their investment and guide continuous improvement.
Building a Secure Future
Zero Trust and SASE together form the foundation of modern secure access. Zero Trust defines how access decisions are made, while SASE ensures those decisions are enforced consistently wherever users connect.
Begin by unifying identity and access controls, then extend enforcement through a cloud-based SASE framework. Automate policies to maintain speed, consistency, and visibility, and measure progress against recognized frameworks to demonstrate both compliance and business impact.
When implemented thoughtfully, this approach strengthens security, simplifies operations, and enhances the user experience—all while giving IT leaders greater control over risk and performance.
Connection works alongside organizations to design and optimize these architectures, combining technical expertise with practical design to help IT and security teams build resilience, agility, and lasting trust in a hybrid world.
SASE and Zero Trust
For more information on Secure Access Service Edge (SASE) and Zero Trust, including how SASE delivery architecture works with Zero Trust security policy to deliver secure networking, read our extensive breakdown.- SASE and Zero Trust overview
- Core components and key benefits
- Practical use cases and real-world scenarios
- Implementation guide